Promenics, Secure System - Reliable Services
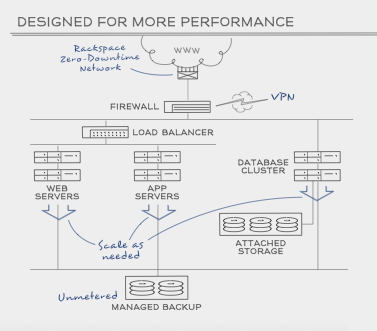
Promenics has partnered with Rackspace, a leading IT infrastructure services provider, to deliver security infrastructure that ensures customer data is never compromised.
SAS 70 Type II Compliant data center
-
Our client's data is hosted in SAS 70 Type II compliant data center.
SAS No. 70 ("SAS 70 Audit") is widely recognized, because it represents that a service organization has been through an in-depth audit of their control objectives and control activities, which often include controls over information technology and related processes. SAS No. 70 is the authoritative guidance that allows service organizations to disclose their control activities and processes to their customers and their customers' auditors in a uniform reporting format.
SAS No. 70 provides guidance to enable an independent auditor ("service auditor") to issue an opinion on a service organization's description of controls through a Service Auditor's Report (also known as a “Type II Report”). The issuance of a service auditor's report prepared in accordance with SAS No. 70 signifies that a service organization has had its control objectives and control activities examined by an independent accounting and auditing firm. The service auditor's report, which includes the service auditor's opinion is issued to the service organization at the conclusion of a SAS 70 examination.
Physical Security
-
Access: Keycard protocols, biometric scanning protocols and round-the-clock interior and exterior surveillance monitor access to every one of our data centers.
Only authorized data center personnel are granted access credentials to our data centers. No one else can enter the production area of the datacenter without prior clearance and an appropriate escort.
Every data center employee undergoes multiple and thorough background security checks before they're hired. -
Precision enviornment: Every data center's HVAC (Heating Ventilation Air Conditioning) system is N+1 redundant. This ensures that a duplicate system immediately comes online should there be an HVAC system failure.
Every 90 seconds, all the air in our data centers are circulated and filtered to remove dust and contaminants.
Our advanced fire suppression systems are designed to stop fires from spreading in the unlikely event one should occur. -
Conditioned Power: Should a total utility power outage ever occur, all of our data centers' power systems are designed to run uninterrupted, with every server receiving conditioned UPS (Uninterruptible Power Supply) power.
Our UPS power subsystem is N+1 redundant, with instantaneous failover if the primary UPS fails.
If an extended utility power outage occurs, our routinely tested, on-site diesel generators can run indefinitely. -
Core Routing Equipment: Only fully redundant, enterprise-class routing equipment is used in Rackspace data centers. Fiber carriers enter our data centers at disparate points to guard against service failure.
-
Network Technicians: We require that the networking and security teams working in our data centers be certified. We also require that they be thoroughly experienced in managing and monitoring enterprise level networks.
Our Certified Network Technicians are trained to the highest industry standards.